cyber resilience
What is cyber resilience?
Cyber resilience is the ability of a computing system to identify, respond and recover quickly should it experience a security incident.
The goal of cyber resilience is to enable an organization to continue operating, even directly after adverse cyber events such as a cyber attacks, natural disasters or security incidents caused by human error. A good cyber-resilience strategy enables an organization to maintain essential business functions, or restore them quickly, after a cyber incident. Cyber-resilience capabilities are essential in IT systems, critical infrastructure, business processes, organizations, societies and nation-states.
To do this, cyber resilience requires a continuous effort and touches on many aspects of information security, such as disaster recovery (DR), business continuity and computer forensics. Cyber resilience is built up over time and refers to the preparations an organization makes to deal with threats and vulnerabilities, the defenses that have been developed, and the resources available for mitigating a security failure after the fact.
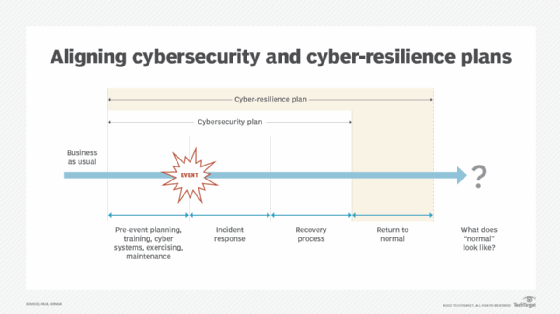
Although they sound similar, cyber resilience and cybersecurity are two separate concepts. While cyber resilience refers to the ability of an organization to identify, respond and recover quickly from a cyberthreat or incident, cybersecurity is the active protection of internet-connected systems from cyberthreats. Cybersecurity standards and frameworks specify how an organization should prepare for and respond to attacks. The two concepts aren't mutually exclusive, however. Both cybersecurity and cyber-resilience plans should be implemented in an organization to create stronger protection against cyber attacks.
Why is cyber resilience important?
Being able to respond to a cyberthreat or incident quickly is one of the main benefits of creating a cyber-resilience plan. The quicker the recovery, the less of an effect a security breach or incident will have on business processes. Ideally, an organization should be able to detect, respond to and recover from a cyber attack quickly enough that it can continue operating without affecting workflow or services -- and with minimal financial loss.
Cyber resilience also increases an organization's cybersecurity posture, which can lessen the number of security incidents. Likewise, the increased data protection can also help an organization comply with regulatory laws.
What are the components of cyber resilience?
The exact components of cyber resilience differ per company; however, some general components might include the following:
- Cybersecurity. As a part of a cyber-resilience strategy, cybersecurity teams work with different tools and policies to help protect an organization's IT systems -- including hardware and software. Cybersecurity software can monitor, detect and respond to cyber attacks. Organizations can follow cybersecurity frameworks provided by groups such as the National Institute of Standards and Technology (NIST) to implement standardized cybersecurity practices.
- Business continuity. Business continuity is an organization's ability to maintain critical business functions during and after a disaster. Business continuity planning creates a risk management process that helps define a plan to reestablish full function to the organization as quickly and smoothly as possible and helps to prevent interruptions to mission-critical services.
- Risk management. Risk management is the process of identifying, assessing and controlling threats to an organization's capital and operations. These risks can stem from a variety of sources, including malicious actors, strategic management errors, accidents and natural disasters. A successful risk management program along with a cyber-resilience plan helps an organization consider the full range of risks it faces.
- Disaster recovery. DR is the set of procedures, policies and tools an organization has in place to respond to and recover from cyberthreats that negatively affect business operations. The goal of having a DR process is to help an organization regain use of critical systems and IT infrastructure as soon as possible after a disaster.
How does cyber resilience work?
For strategic planning, a key element of cyber resilience is a deep understanding of risk -- which means going beyond IT planning to make limiting risk exposure an integral part of the strategy. To capitalize on the paradigm shift from cybersecurity to cyber resilience, businesses should focus their resources on the cyber-risks that are likely to have the biggest impact, and concentrate on the metrics that provide insight into and help predict them.
A cyber-resilience framework should be built on a strategy surrounding the following steps as defined by NIST:
- Identify. Organizations should look for potential security exposure indications proactively. This includes monitoring for potential software vulnerabilities and misconfigured devices.
- Protect. Organizations should build up their infrastructure to deal with the potential for cyberthreats and use cybersecurity tools to help prevent potential harm to critical infrastructure and data.
- Detect. Security tools and processes should be fine-tuned for incident detection and to identify potential risks and irregularities. Tools and processes in use should be able to monitor critical systems for internal, external, malicious or natural threats.
- Respond. Data from any security incident should be collected and analyzed to help organizations make better-informed decisions.
- Recover. To avoid interruption to business, organizations should have systems in place to rapidly restore data and to recover mission-critical systems. For example, this could include keeping a backup of customer data in the cloud, hosted in a different geographic location from the organization.
The cyberthreat landscape is constantly changing, and organizations should be able to adapt to any given circumstance. For example, once an organization recovers from an incident, it should modify its security procedures and design a security strategy to defend against the same issue. Organizations should also be proactive and continually review their security posture.
Addressing resilience extends beyond IT or information security. To ensure greater efficiency and effectiveness, technology and strategic leaders should be involved in an overall cyber-resilience approach as a key part of their long-term strategy, including outlining which technologies a business will implement in the next five, 10 or more years.
Cyber resilience is an important aspect of keeping an organization safe from malicious or natural threats. Learn how to build a cyber-resilient culture.