adaptive multifactor authentication (adaptive MFA)
What is adaptive multifactor authentication (adaptive MFA)?
Adaptive multifactor authentication (MFA) is a security mechanism intended to authenticate and authorize users through a variety of contextual authentication factors. Adaptive MFA essentially poses different sets of authentication requirements based on the user group attempting to access the application or data, as well as the risk profile or risk level involved in those users' access. Adaptive MFA is sometimes called risk-based authentication.
A traditional authentication process involves usernames and passwords and is generally considered to provide only modest security. Credentials are easily hacked. Anyone in possession of valid credentials can access and potentially alter or steal data.
Multifactor authentication rose to address the limitations of traditional authentication by requiring an additional, often physical, item to validate the user's identity. For example, a traditional login might also require entering a unique one-time code sent to a smartphone or email address, which would only be in the possession or control of the actual user.
MFA combines "something you know," such as passwords, with "something you have," such as a smart device. However, existing MFA still only provides a static security posture. Even though MFA can dramatically enhance security, it does not consider the requirements or situational context of user access.
Adaptive MFA takes this process further by coupling MFA practices with security policies and a dynamic, or adaptive, assessment of context and risk.
For example, consider a knowledge worker who requires access to business applications and data in the office during normal business hours. Adaptive MFA would look at the security policy for that user and group, then determine that access should be granted on the local area network (LAN) during regular weekday business hours.
If a login attempt is made within those criteria, the resulting risk assessment would be within the established risk profile for that user. No additional security challenges would be presented because the risk posed by that user is low and the confidence in that user's activities is high.
If a login attempt is made outside of those criteria -- on a weekend, outside of normal business hours, from an IP address not on the LAN, or involving multiple incorrect password attempts -- the adaptive MFA system might determine a higher risk assessment that is outside of the established risk profile for that user. It would then present additional security challenges.
Similarly, an adaptive MFA system might impose different security challenges for different user groups, elevating the complexity or scope of security challenges based on risk. For example, an IT administrator or an outside vendor partner might face more frequent and stringent challenges from an adaptive MFA system than a local employee in HR or payroll.
Benefits of adaptive MFA
Adaptive MFA promises two principal benefits to the enterprise.
1. Improved security
The fundamental justification and purpose of adaptive MFA is to improve enterprise security by ensuring only authorized users can access business applications and data. Adaptive MFA facilitates this goal in a more comprehensive and organized way that considers and adapts to established risk factors. Static MFA does not recognize these factors.
2. Better productivity
Common MFA requires the same credentials and MFA interaction every time a user logs on. This can be disruptive and onerous, especially when a user must make many logins, such as a clinician moving between exam room computers throughout the day. Adaptive MFA can pose fewer challenges for users that behave in expected ways.
For the clinician example, adaptive MFA might allow a doctor to log in once or only every few hours during the day. They can move seamlessly between computers simply by swiping their badge at each station within the facility. This reduces the potential friction of common MFA schemes.
How does adaptive MFA work?
Adaptive MFA works by coupling the authentication process with a risk analysis. When a user attempts to login, the system checks the user's purported identity and user behavior against an established risk profile. As the user attempts access, they receive a risk factor score such as low, medium, and high. The higher the risk score, the more information that the user must provide to complete their authentication and move on to authorization.
Figure 1 shows a typical logic flow for an adaptive MFA process.
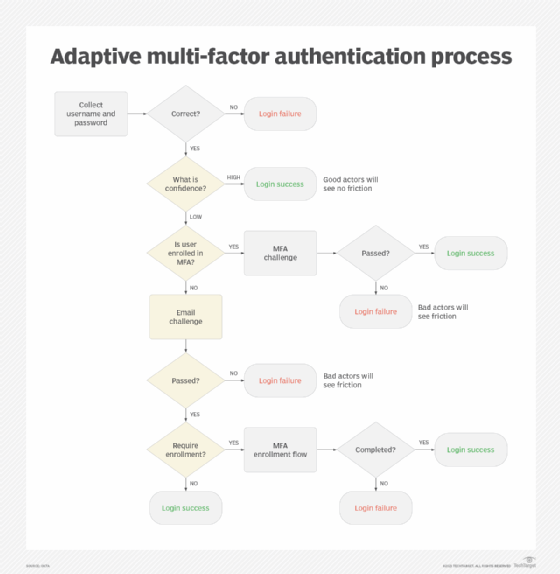
It's important to note that adaptive MFA operates throughout the users' login session, not just during the initial login. User behavior and risk can be assessed constantly.
A risk profile, also called an adaptive MFA policy, typically outlines the "normal" criteria for the successful login of each user group. These factors can be detected or determined during the login process. The more policy factors that align, the lower the risk. There are many potential factors to consider for an adaptive MFA policy including:
- Physical location. This includes IP addresses or user geolocation data.
- Geo-velocity. This can indicate the physical distance between consecutive login attempts. Multiple attempts from impossibly distant locations will suggest serious risk.
- Time of day. This can include a normal shift or business hours for the user.
- Device type or operating system. For example, the policy might look for a tablet running an Android operating system or a laptop running Windows 11.
- Account history. Typical login frequency and duration over the last six months are potential factors to base login criteria on.
- Detection of malware or anti-malware software. The presence of either can influence login criteria. For example, MFA policies might check that anti-malware software is installed in accordance with business requirements.
- Consecutive login failures. These are a classic sign of unauthorized access.
- User role. User roles have a direct impact on risk. Sensitive roles will receive more scrutiny from adaptive MFA systems.
- Access sensitivity or attempted action. This will watch over the applications and data a user attempts to access, then flag significant risk when the user attempts to access unauthorized apps and data or take other actions outside of their established policy.
The user's login authentication attempt is assessed against established policy and will result in several possible outcomes:
- Access allowed. The user has met the requirements of the adaptive MFA policy and demonstrated their identity successfully enough to gain access.
- Challenged. The user's risk score is higher than the established risk profile, and authentication will require successful responses to one or more security challenges.
- Access denied. The user has failed to meet the requirements of the adaptive MFA policy and any subsequent security challenges. Authorization is denied. This will typically generate a security log and alert events for further investigation and remediation.
When a user's interactions raise their risk score, an adaptive MFA system might require additional information to complete or update the authentication process. Common challenge requests might include the following:
- Security challenge questions. Users may be required to answer one or more security questions, which they selected when creating their account. Only the user knows the answer to those security questions.
- One-time password codes. The user might be asked to receive and enter a one-time password (OTP) sent either to the user's email or phone using an SMS, or short message service, text. This relies on the user possessing a smart device or control over their email account as proof of their identity.
- Push notifications. The system sends a notification to the user's registered mobile device and the user acknowledges receipt of the mobile push notification. This is a variation of OTP SMS codes.
- Facial recognition. The system might require facial recognition, such as a photo of the user or capture from a live video stream, to validate their identity.
Machine learning (ML) and artificial intelligence are increasingly prevalent in adaptive MFA as a means of learning user behavior. As it learns "normal" user behaviors, ML spots unusual variations in user behavior and flags attempted actions as accidental or malicious. This lets the adaptive MFA system take a more proactive role in stopping unauthorized actions, posing additional challenges and maintaining security throughout the user's login session.
Practices for implementing an adaptive MFA policy
There are few formal guidelines or best-practices for creating an adaptive MFA policy. The concept of adaptive security is relatively new, and the security needs of every enterprise differ dramatically. However, several practices can be implemented as a starting point for adaptive MFA policy.
Consider default policy as a starting point
Adaptive MFA providers will typically provide a default policy that dictates basic adaptive behaviors. A default policy might be a good option for organizations just getting started with adaptive security techniques. As an example, ServiceNow provides default policies as either of the following:
- Step-up MFA policy, which will enforce MFA when the policy step-up conditions are true.
- Step-down MFA policy, which will bypass MFA when the policy step-down conditions are true.
Carefully match definitions to actions
Adaptive MFA is a relatively narrow security function with one principal goal: impose security requirements or responses that are appropriate for a given risk level. There are typically four major risk levels:
- Very High. A user poses a critical risk to the business because the user was acting in a suspicious manner or the access device is unknown, is not trusted or hosts a detected form of malware. These users are typically blocked by default.
- High. A user poses some risk and must confirm their identity each time they attempt to access an adaptive MFA-protected app or data. These users are typically forced to use MFA on every access.
- Medium. A user must confirm their identity once per session when they first log in. Subsequent authentication requests do not require MFA. When the session expires, new MFA is required.
- Low. A low-risk user typically does not need to satisfy MFA. Common usernames and passwords are accepted for authentication.
There are also numerous possible responses the security architecture can produce:
- Allow. User access is granted.
- Allow (override). User access is allowed to the exclusion of all other decisions in the policy.
- MFA per session. MFA is required on a per-session basis.
- MFA always. MFA is always required for the user, even in the same session.
- MFA (override). MFA is required to the exclusion of all other decisions in the policy.
- Block. User access is denied.
- Block (override). The user is blocked to the exclusion of all other decisions in the policy.
Finally, a suitable MFA mechanism must be selected for situations when MFA is required. There are numerous methods available for MFA:
- Email OTP.
- A password-less standard such as Fast Identity Online 2.
- SMS OTP.
- Time-based OTP.
- A vendor-based mechanism, such as IBM Verify.
- Voice OTP.
- Visual OTP, such as a photo of the user.
This combination of risk levels, responses and MFA options, when called for, comprise most of an adaptive MFA policy.
Review the policy
An adaptive MFA policy should be created and reviewed by a collaborative group of IT, business and legal leaders to ensure the resulting policy can be implemented while meeting the enterprise's business goals and regulatory/compliance obligations.
Update the policy regularly
The security needs of a business are always evolving as new threats are met with new technologies. An adaptive MFA policy should be reviewed periodically to ensure it continues to meet business and legal requirements while employing new and emerging technologies to further enhance security while reducing user friction.
