
How API attacks work, plus 5 common types
A growing number of API attacks put enterprises at risk of serious data breaches. Learn how these attacks work, and explore some API security best practices.
API attacks are on the rise, opening organizations to new security risks.
Traditional website-based cyberattacks target the application itself, but as companies expose a growing number of website APIs to the internet, these connections are increasingly drawing the attention of threat actors.
An API lets software communicate with other software to share data and functionality. For example, an API might let a user log in to an application with credentials from a third-party account, such as Facebook or Google.
An API key authorizes a connection between software programs, acting like a password to identify the application calling the API and prove it has access permissions.
API requests are similar to the access requests users send from their browsers, meaning many attacks that work against websites can compromise APIs as well.
5 types of API attacks
Malicious hackers employ a number of API attacks and API abuse techniques. These include the following.
1. Injection attacks
An API is vulnerable to SQL injection or cross-site scripting (XSS) if developers don't properly sanitize its query parameters to ensure the API sends and receives only appropriate data.
In injection attacks, cybercriminals insert malicious code into their queries to trick the API into granting unauthorized access to sensitive data. They can then steal, modify, delete and replace that information as they choose.
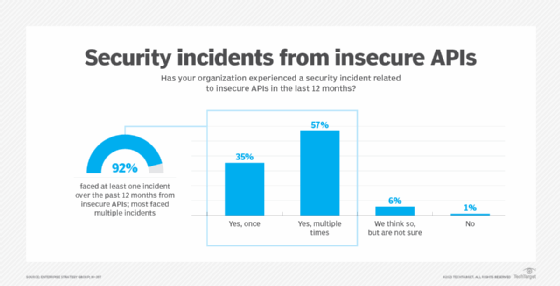
2. Broken access control attacks
In some cases, threat actors can bypass standard access control guardrails by interacting with target APIs directly and exploiting their security vulnerabilities. At worst, APIs with broken authentication and authorization controls set the stage for massive data breaches.
In a broken object-level authorization attack, for example, an API might successfully authenticate a user through a userID value in the API request but accept a different ID in the query parameter.
If the API does not validate that the authenticated user should have access to the requested data -- i.e., that the userID in the request matches the userID in the query -- then an attacker can easily access details of any other user's account.
And if API rate limiting isn't in use -- restricting the number of calls one user can make in a given time frame to reduce the attack surface -- then the threat actor could exfiltrate massive amounts of sensitive information.
In some past attacks, vulnerable API endpoints did not require any user authentication at all, leaving them wide open to malicious hackers.
3. Excessive data exposure
Organizations that do not manage their APIs effectively often allow too many APIs -- for example, old or test versions -- to be exposed to the internet. In some cases, such APIs send too much information back when they receive requests, potentially exposing sensitive data.
4. DoS and DDoS attacks
If an API is not protected from denial-of-service and distributed denial-of-service attacks, bad actors can launch a brute-force attack, in which they send a huge volume of data to the API and cause the entire website to stop responding.
5. Third-party attacks
Attackers can also target APIs through third parties. A malicious hacker might be able to compromise a trusted partner that has a legitimate API key, for example, and use it to access the target API.
Defending against API attacks
Organizations should defend APIs as they protect any traditional web application -- by following application security best practices and deploying appropriate cybersecurity measures. Consider the following ways to mitigate API vulnerabilities:
- Sanitize all query parameters that the API can interpret to prevent XSS, SQL injection and other similar attacks.
- Institute strong user authentication and authorization mechanisms to help prevent a malicious user from accessing data through an API.
- Ensure DoS and DDoS security software protects not only the main website, but APIs as well.
- Keep an accurate inventory of APIs exposed to the internet, and know which third-party organizations and users have access. Assess what type of and how much information the API returns to the end user, and ensure it's no more than necessary.
Rob Shapland is an ethical hacker specializing in cloud security, social engineering and delivering cybersecurity training to companies worldwide.








