
Getty Images
ARP vs. RARP: What's the difference?
Network devices use ARP to map IP addresses to MAC addresses. RARP, which is less common, accomplishes the reverse and enables network devices to map MAC addresses to IP addresses.
When devices communicate on a network, the network interface card of the sending device breaks data into frames. The frames include the source and destination MAC addresses, also known as physical addresses.
The destination MAC address indicates the next physical hop in the data transfer process. The source MAC address is the unique identifier of the device's NIC that sent the packet. Data transmissions also include the IP addresses of the source and destination devices. The source device knows its own MAC and IP addresses but needs to discover the destination's addresses.
Address Resolution Protocol (ARP) provides this information because it maps physical MAC addresses to logical IP addresses. In contrast, Reverse ARP (RARP) accomplishes the reverse of ARP. RARP enables network nodes without IP addresses to request one. However, RARP has become obsolete and is rarely used in modern networks.
ARP explained
ARP enables systems to link physical MAC addresses with logical IP addresses. When MAC addresses and IP addresses correlate with each other, network nodes can efficiently route data to its intended destination.

When a device is ready to send data to another, it uses DNS to translate the destination's hostname to an IP address. It then uses ARP to find the MAC address related to that IP address. The data frame contains both addresses.
ARP broadcasts a query on the local segment to ask a question like, "Who has this IP address?" The system with the matching IP address responds with its MAC address. The source device also automatically caches the MAC and IP address maps for future use.
RARP explained
RARP achieves the opposite goal of ARP: Devices use RARP when they know their MAC addresses but need to obtain IP addresses. RARP was initially developed as a way for diskless systems without permanent storage to acquire IP addresses.
Unlike ARP, which is a part of most network transmissions, RARP has mostly disappeared from modern network use. Dynamic Host Configuration Protocol, which assigns IP addresses to network devices and nodes, has replaced most of RARP's functionality in modern networks. DHCP has greater flexibility, ease of use and automatic configuration, among other improved capabilities over RARP.
Compare ARP vs. RARP
ARP and RARP work with the same addresses but accomplish different goals:
- ARP. ARP relates a known destination IP address to an unknown destination MAC address.
- RARP. RARP relates a known source MAC address to an unknown source IP address. It is less common in modern networks.
Use arp commands to view MAC address information
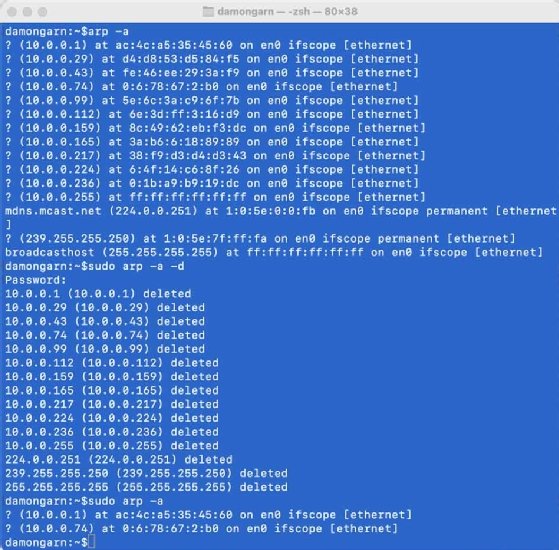
The arp command displays and lets network administrators manage their system's ARP cache. This command contains several options, based on what network administrators need. Network administrators often use ARP to view the cached MAC address-to-IP address mappings. They can also add and remove mappings manually.
ARP commands include the following:
- arp -a. View the ARP cache.
- arp -s {ip} {mac}. Configure a static mapping.
- arp -d {ip}. Remove a static mapping.
Use the arp man page or arp command to view the help file.
While network administrators can statically map IP and MAC addresses, it's usually unnecessary unless they need to modify any entries.
The arp command is useful for network troubleshooting, especially if many IP addresses on the segment have changed recently. In that case, network professionals might worry that the local system retains an outdated MAC-to-IP address mapping in its cache, which could send data to the wrong destination system.
Network administrators can delete specific mappings from the cache, but it's typically easier to clear them. ARP queries don't overload modern networks, so it isn't a concern to force clients to recache many MAC addresses.
Use ARP with other network troubleshooting tools
Packet sniffers, like Wireshark and tcpdump, are useful to find or view MAC addresses. These tools intercept and display network traffic, and they're best known for their ability to show the user data that transfers across a network.
Wireshark and tcpdump can also display the data frame's header information, which includes both source and destination MAC and IP addresses. Network administrators use this information to help identify misconfigured or spoofed nodes.
People spoof MAC address for both legitimate and malicious reasons. Spoofing an address hides the NIC's actual MAC address in favor of a fake one. This can protect privacy, but it can also redirect network traffic to an unauthorized node. When network administrators combine tools like Wireshark with ARP, they can detect and remove spoofed devices if necessary.
The Nmap network scanner doesn't show MAC address information with the standard scans. However, it can be useful to identify nodes on the network with Nmap and use the arp commands to relate them to the results.
Wrap-up
RARP has mostly disappeared from today's networks due to the improved configurability of DHCP. However, ARP is still a critical part of IPv4 communications. The two protocols might appear to achieve similar ends, but they differ significantly.
Most IPv4-based network transmissions begin when the source computer acquires the destination computer's IP and MAC addresses. IPv6 network communications don't use ARP for this, though, because of potential security vulnerabilities. Instead, IPv6 nodes use neighbor discovery.
Nevertheless, ARP is an essential protocol that can help network administrators with their network troubleshooting process and help them better understand device identities.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to TechTarget Editorial and CompTIA Blogs.







