7 risk mitigation strategies to protect business operations
Companies facing a multitude of business risks have various options to mitigate them. Here are seven mitigation strategies to minimize the business impact of risks.
Without risks to manage and mitigate, life in business would be a lot easier. Various internal and external business risks can affect financial performance and disrupt the four critical elements that enterprises need to operate: people, processes, technology and facilities. Each element faces risk-driven threats and vulnerabilities that must be dealt with to avoid potential business problems.
As part of an enterprise risk management program, mitigation efforts must not only identify risks, but also develop a plan to address them. Taking some risks is a necessary part of doing business, and effective risk mitigation doesn't completely eliminate them. Instead, it aligns with an organization's risk appetite, which specifies the amount of risk that executives are collectively willing to take to achieve the business goals they've set for the company.
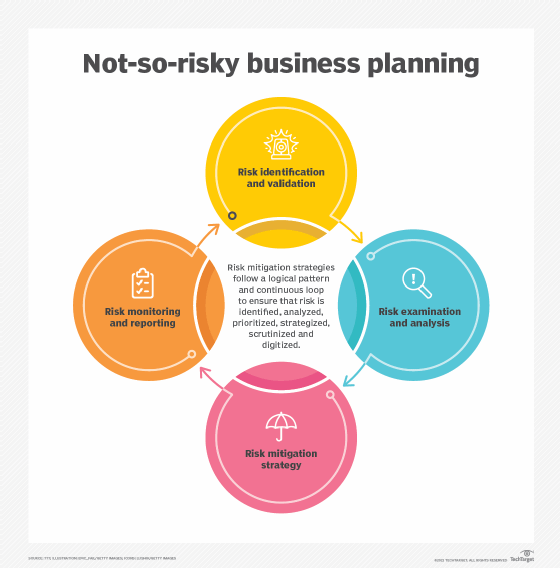
Risk mitigation planning
To address identified business risks, they must be analyzed to determine the likelihood of an occurrence and its potential effect on business processes, employees and financial results. A priority list should be created to rank each risk according to how likely it is to occur and how severe its business impact would be. For example, a high-probability event that has little or no impact on the organization, such as an employee calling in sick for one day, will be treated much differently than a low-probability, high-impact event like an earthquake or a flood.
Risk management teams can also create a risk assessment matrix that provides a visual representation of the potential business impact of different risks. Also known as a risk heat map, it plots risks in a color-coded matrix to help business executives and risk managers develop a mitigation plan.
Common risk mitigation strategies
Once a plan has been established and an overall risk management framework is in place, decide what strategies you'll use to mitigate specific risks, threats and vulnerabilities and then document the necessary actions. The following are the seven most widely used mitigation strategies for business risks.
1. Accept and deal with the risk
The enterprise deems a risk sufficiently non-threatening to business operations and can effectively respond to a threat occurrence. Examples of risk acceptance include accepting the risk of production schedule delays that aren't expected to damage the business, accepting adjustments to budget expectations that could affect business operations and accepting the need for employees to continue working remotely.
2. Avoid the risk
The enterprise makes a conscious decision to avoid dealing with a specific risk and its outcome. Examples of risk avoidance include identifying specific risks and suitable remedies or alternate processes to avoid potential negative outcomes, identifying all expected and unexpected costs for a project and then taking needed steps to prevent it from going over the budget, and identifying qualified alternate members of a project team who can step in when necessary to avoid delays.
3. Challenge the risk
When an identified risk emerges, the enterprise slows or terminates the event to an acceptable level before it progresses to the point where it can damage the business. Examples of risk challenge include evacuating employees in advance of a severe storm to minimize any potential risk to life, launching emergency power systems when a power outage occurs to minimize the disruption to operations, and identifying a cybersecurity threat and immediately blocking the malware before it can enter the company's internal computing environment or isolating it to stop it from spreading.
4. Prioritize the risk
If more than one risk event occurs at the same time, such as a severe storm and a power outage, the organization establishes a priority list of actions to address the most critical risks first. Examples of risk prioritization include activating backup procedures to protect systems and data due to an impending flood and its potential water damage to an office as well as extinguishing a fire, shutting down power supplies and notifying the power company and fire department when a lightning strike causes a transformer to explode.
5. Control and manage the risk
As a core part of the risk management process, the enterprise deals with specific risks by documenting planned management actions, testing them to ensure that they're appropriate and then implementing them. Examples of risk control and management include establishing policies for physical security and data protection, developing business continuity and disaster recovery plans, and devising project management methods to ensure that project delivery schedules are maintained and cost overruns are prevented.
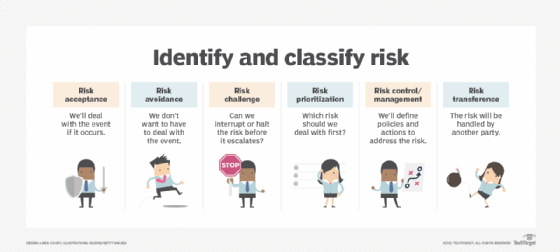
6. Transfer the risk
Difficulties associated with a specific risk are transferred to another party, often insurance companies for coverage such as cybersecurity liability insurance. Examples of risk transfer include buying business interruption insurance to handle unplanned expenses in the aftermath of a cyber attack, contracting with a project management company to handle oversight of a particularly difficult project, and engaging an outside auditor to attest that corporate reports and disclosures on environmental, social and governance initiatives are accurate.
7. Document and monitor the risk
All aspects of enterprise risk management, such as risk profiles, risk factors and inherent risk, should be carefully documented at every stage of the process. Likewise, all risk-related activities must be monitored to ensure that any issues are quickly identified and addressed. Examples of risk documentation and monitoring include monitoring risk management costs to prevent unplanned expenses, monitoring operational activities to avoid compliance issues, and using intrusion detection systems and firewalls to monitor incoming and outgoing data traffic to identify suspicious data packets that could signal a cyber attack.
Be prepared to mitigate business risks
Risk mitigation strategies are an important part of an enterprise risk management program. With multiple strategies available, risk managers have plenty of tools to deal with business risks in the enterprise. While different approaches may be used for various risks, definitive mitigation strategies should be in place and ready to use. Otherwise, an organization faces the prospect of failed risk management efforts, and that's a risk no company should take.







