
It has been reported that a GPU Miner Trojan is being installed along with the popular Andy Android emulator and its users are rightfully concerned. This miner reportedly will use the graphics processing unit, or GPU, on the computer's graphic's card in order to mine cryptocurrency.
In a post on Reddit by user named TopWire. it was stated that Andy was installing a GPU Miner Trojan without a user's knowledge. This Miner would be installed as C:\Program Files (x86)\Updater\updater.exe and when launched would use up the GPU on the computer. The user also posted a YouTube video showing this behavior, which is displayed at the end of this article.
What is concerning is that the Reddit poster has stated that he has tried to bring this up to the Andy team via the Facebook user group numerous times and has been repeatedly kicked out each time.
What happens when you install Andy?
When I downloaded and tested the current Andy executable, I automatically saw something that rang alarm bells. It was using an adware bundler for its installer, which are known to sometimes perform sneaky installs of miners onto user's computers without their knowledge or permission.
According to VirusTotal, the Andy installer is being detected as an InstallCore variant, which is a known adware installer that present users with various "offers" when installing free software. These installers allow developers of free software, such as Andy, to generate revenue each time someone installs their program.
When testing the current Andy installer, I was presented with offers for Avast, the Search Manager Chrome Extension, and WinZip, which I declined.

Even after declining all of these offers, a program was still installed on my test computer. Guess what? It was a file called C:\Program Files (x86)\Updater\updater.exe. For me, though, the program just generated an error when it was executed.

If this file is indeed a GPU miner, I could be receiving this error because I am running it on a virtual machine that does not have a dedicated graphics card on it. When scanning it using VirusTotal, it does not indicate that it is a miner.
The updater.exe file posted by the Reddit, though, is clearly detected as a Miner. Furthermore, when examining the strings found in the Updater.exe Miner variant posted on Reddit, its strings indicate it is one as well.
{"id":%llu,"jsonrpc":"2.0","method":"submit","params":{"id":"%s"
Unauthenticated
[0m
,"job_id":"%s","nonce":"%s","result":"%s","inst_date":"%s","userID":"%s"}}
[31m
[33m
job_id
[01;37m
target
job
[01;30m
blob
coin
coin
variant
variant
Where is the installer coming from? The installer or Andy?
When testing the Andy installer using the sandbox site Any.Run, you can see a file called GoogleUpdate.exe being executed. When executed with the command line "GoogleUpdate.exe /svc" it launches another program named UpdaterSetup.exe, which installs the Updater.exe program and configures it to automatically start when you log into Windows.
This GoogleUpdate.exe program has a description of "AndyOS Update", which indicates it's part of Andy. Why it is named GoogleUpdate is not known, but I feel it is strange.
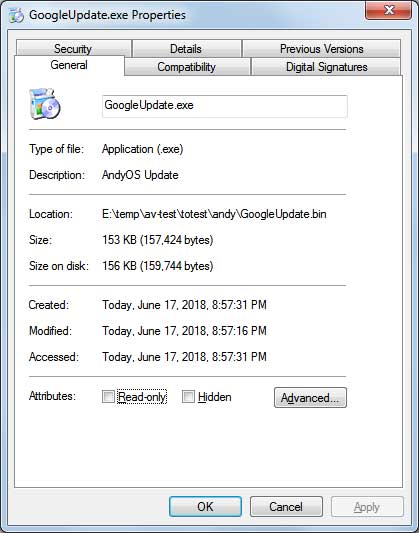
Furthermore, the GoogleUpdate.exe file is code signed by "Andy OS Inc". This indicates that the file belongs to Andy OS Inc or at least was intentionally signed by them.
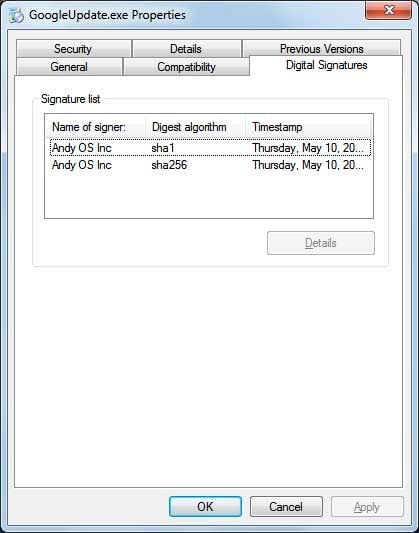
Finally the signature further indicates that it belong to Andy OS Inc.
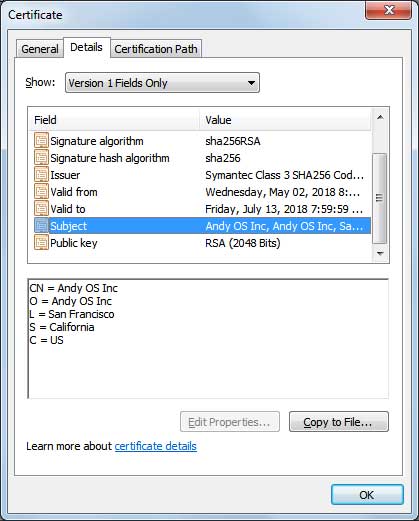
As the GoogleUpdate.exe is signed using a signature that is owned by Andy OS Inc, it would indicate that this file it one that belongs to them.
While Bleeping Computer has not been able to corroborate that Andy is installing Miners onto user's computers, we could confirm that it is creating an Updater.exe executable as described by the Reddit user's post. For now, it is advised that users do not install Andy until further information is given by the Andy developers.
Below is the video created by TopWire that demonstrates what he saw when installing Andy.
Bleeping Computer has reached out to both the marketing contact and support contacts at Andy OS for comment, but have not heard back at the time of this publication.
This is a developing story and will be updated as more information becomes available.




Comments
GT500 - 6 years ago
It sounds like at least some VMware products support CUDA and OpenCL, however I've read somewhere that you have to go into settings and "virtualize" the video card (assign it to a VM) in order for it to work. I can't find any such settings in VMware Workstation 14, so I'm not certain what they were talking about. I did find an article VMware posted in 2011 about CUDA/OpenCL working in ESX, but I didn't look into it enough to know if it works in VMware Workstation.
TomClancy - 6 years ago
VMware Workstation doesn't support GPU passthrough, only ESXi does.
BeckoningChasm - 6 years ago
The file property and code signatures indicating ownership--could those be faked? I don't use Andy (never heard of it before now) so I'm just curious.
Lawrence Abrams - 6 years ago
Can't be faked, but it's remotely possible that a code signing company could have issued a certificate to a wrong company/individual. Doubtful though.
survivor303 - 6 years ago
normally googleupdate.exe is google chrome/other google product update agent, so now andy is trying to hide its malware from user. because googleupdate.exe can show multiple individual process in taskmanager, and by default taskmanager isnt show full path of the file, so normal user dosnt think much more about it and let it be.