What Is Encryption? Algorithm, Public Key And Everything Else
Encryption disguises information as random data. Internet security requires encryption.
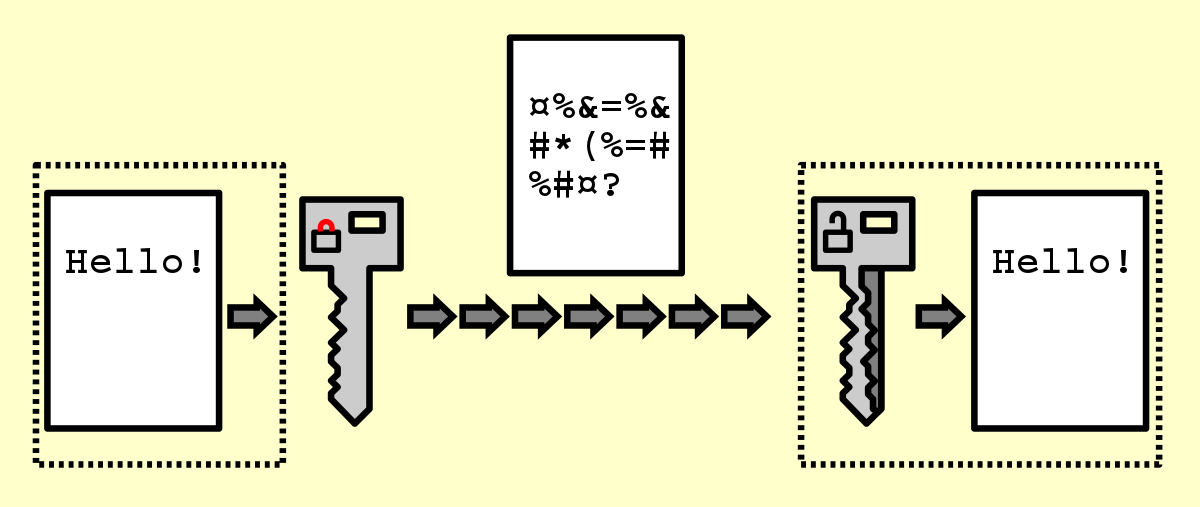
A computer technique known as data encryption converts plaintext or cleartext (material that has not been encrypted and is readable by humans) into ciphertext (data that has been encrypted) that can only be accessed by authorized users who have the appropriate cryptographic key. Encryption, to put it in its most basic form, changes readable data into some other form that can only be decoded and viewed by those who know the correct password. This process is an essential part of the digital transformation process.
What exactly is encryption?
Data Encryption is a method of encoding data in such a way that it can be understood by only those who have been granted access to the data. In a more technical sense, it is the process of transforming plaintext, which can be read by humans, into ciphertext, which cannot be understood by humans. Encryption, in its most basic form, involves taking data that can be read and modifying it in such a way that it looks to be random. The usage of a cryptographic key, which is defined as “a set of mathematical values that both the sender and the recipient of an encrypted message agree on,” is necessary for the process of encrypting a communication.
A party that obtains the encrypted data and possesses the appropriate key is able to decrypt the data and turn it back into plaintext. Despite the fact that encrypted data appears random, encryption works in a logical and predictable fashion. A really secure encryption system will make use of keys that are so complicated that it is extremely unlikely that a third party will be able to decrypt or break the ciphertext by using brute force, or, to put it another way, by trying to guess the key.
It is possible to encrypt data “at rest,” when it is being stored, as well as “in transit,” when it is being transmitted to another location.
ad
Why data encryption is necessary?
Privacy: Encryption protects one’s privacy by ensuring that no one other than the intended recipient or the legitimate owner of the material may read communications or data that is at rest. This protects the privacy of users by preventing sensitive data from being intercepted and read by attackers, ad networks, Internet service providers, and in some situations, governments.
Security: Encryption helps prevent data breaches, whether they occur while the data is moving or when it is sitting at its destination. If the hard disk of a company device is encrypted correctly and that device is then lost or stolen, the data that is stored on that device will not be compromised. In a similar vein, encrypted communications allow for the sharing of sensitive data between the persons conversing without the risk of the data being leaked.
Integrity: Integrity of the data is preserved because to encryption, which also helps stop hostile activities like on-path attacks. Encryption is used to ensure that data sent via the Internet has not been viewed or altered en route by anybody other than the intended recipient. This protects sensitive information.
Regulations: Because of all of these reasons, many industry rules and government regulations require businesses that handle user data to maintain that data encrypted. This requirement applies to both private and public firms. HIPAA, PCI-DSS, and the General Data Protection Regulation are a few examples of regulatory and compliance standards that mandate the use of encryption.
RC4: Rivest Cipher 4 was created by Ron Rivest in 1987 for RSA Security. RC4 abbreviates it. A Stream Cipher. Stream Ciphers encrypt data byte by byte. RC4 is a popular stream cipher since it’s simple and fast. Variable-key stream cipher with byte-oriented operations. It has 64 or 128-bit keys. It is used in SSL, TLS, and IEEE 802.11 wireless LAN standard.
What is a key In the cryptography world?
A string of bits that is utilized by a cryptographic method to convert plain text into cipher text or vice versa is referred to as a cryptographic key. This key is never revealed to anyone, which keeps all communications secret and safe.
A cryptographic key is the most essential component of any activity using cryptography. Encryption and decryption are just two of the many pairs of operations that are built into numerous cryptographic systems. A key is a piece of data that is included as part of the variable data that is given as input to a cryptographic algorithm in order for it to carry out an operation of this kind. When a cryptographic scheme is well-designed, its level of safety is directly proportional to the level of safety afforded to the keys that are employed.
Differences between a public key and a private key in encryption
Data can be encrypted and decrypted using asymmetric encryption cryptography by utilizing a public key and a private key respectively. The public key is the one that may be freely shared with others, while the private key is the one that only the owner knows. A person can encrypt a message in this manner by using the receiver’s public key; however, the message can be decoded only by the receiver’s private key.
What are types of Encryption?
There are two main types of encryption:
Symmetric encryption and asymmetric encryption are the two types of encryption that are utilized on a broad basis today. The meaning of the term is determined on whether or not encryption and decryption make use of the same key.
Symmetric Encryption
The process of encrypting and decrypting data using symmetric encryption methods requires the use of the same key. This indicates that the sender of the encrypted data or the computer system that encrypted the data must reveal the secret key to all authorized parties in order for those parties to be able to decrypt the data. Since symmetric encryption can normally be implemented more quickly and with less difficulty, it is the method of choice when it comes to encrypting large amounts of data in bulk.
The Advanced Encryption Standard (AES), which was established as a federal standard in the United States by the National Institute of Standards and Technology (NIST) in the year 2001, is one of the symmetric encryption ciphers that is used the most frequently. 128 bits, 192 bits, and 256 bits are the three distinct key lengths that are supported by AES. The key lengths influence the number of potential keys. To break any AES key length would need levels of computer power that are not currently imaginable and are not expected to become imaginable in the foreseeable future. The Advanced Encryption Standard is widely utilized all throughout the world, especially by government agencies such as the National Security Agency (NSA).
Asymmetric Encryption
The method of encryption known as asymmetric encryption, which is also known as public key encryption, makes use of two keys that are separate from one another but are mathematically related to one another: a public key and a private key. In most situations, the public key is broadcasted for everyone to see and may be utilized by anyone, but the private key is safely stored and can only be accessed by the person who owns the key. Sometimes the data is encrypted not once, but twice; the first time, it is encrypted with the sender’s private key, and the second time, it is encrypted with the recipient’s public key. This ensures that the data can only be decrypted by the intended recipient, and it also verifies that the sender is who they say they are. Asymmetric encryption is therefore more flexible for some use cases because the public key (or keys) can be easily shared. On the other hand, asymmetric encryption requires more computing resources than symmetric encryption does, and these resources increase with the length of the data that is being protected.
As a result, a hybrid strategy is quite common: a key for symmetric encryption is developed and utilized in order to safeguard a quantity of info. After that, the symmetric key is encrypted utilizing the recipient’s public key, and it is then packaged along with the payload that has been symmetrically encrypted. Using asymmetric encryption, the recipient first decrypts the relatively short key, and then using symmetric encryption, they decrypt the actual data.
The RSA cipher, which was developed in 1977 and named for its three creators—Ron Rivest, Adi Shamir, and Leonard Adleman—is currently among the most popular asymmetric encryption algorithms. The RSA method is still one of the most used asymmetric encryption techniques in use today. The RSA cipher, along with all other forms of asymmetric encryption in use today, is based on the process of prime factorization, which involves multiplying two huge prime numbers to produce a number that is even greater. When the appropriate key length is utilized, cracking RSA is an exceedingly challenging task since it requires determining the two original prime numbers from the multiplied result, which is a challenging mathematical problem.
What is encryption algorithm?
A method for transforming regular data, often known as “plaintext,” into a secure encrypted message that is referred to as “ciphertext.” It is possible for the ciphertext to be kept in storage or transmitted over insecure networks without the information it contains being revealed to unauthorized individuals.
In order to execute the calculations, each algorithm makes use of a “key,” which is a string of bits that is created at random and is also known as a “cipher.” It will be more difficult to crack the code and decipher the contents if the key is larger (has more bits). This is because a larger key allows for the creation of a higher number of alternative patterns.
The block cipher approach, which codes set blocks of input, is utilized by the vast majority of encryption algorithms. Some people prefer to employ the stream approach, which encrypts each bit individually. For more information, see algorithms, modes of operation, cryptography, security protocols, stream ciphers, and block ciphers.
3DES
This is a significant improvement over DES; it employs three separate applications of the DES cipher and operates in EDE mode, which stands for “encipher-decipher-encipher,” using keys that are completely unrelated to one another. It is an outer-CBC that is used. Although it is very, very slow, this method is considered to be very secure (large banks use it to protect valuable transactions), and big banks use it to protect valuable transactions.
Blowfish
Bruce Schneier, owner of the company Counterpane and author of the book Applied Cryptography, is responsible for the development of the Blowfish encryption algorithm, which features a high level of security. It can move at a very high speed, is regarded as secure, and can withstand linear and differential analysis. This is the cipher that I prefer to use personally.
Twofish
Twofish is the successor of Blowfish, and just like its predecessor, it employs symmetric encryption, which means that only a single key of 256 bits is required to decrypt data. This method is one of the most efficient algorithms for encrypting data, and it works wonderfully in both software and hardware settings. It was a finalist for the competition held by the National Institute of Technology and Science (NIST) to identify a successor for the encryption algorithm used by the Data Encryption Standard (DES), and it was released at the time that the competition was held. In the end, the Rjindael encryption algorithm prevailed over the Twofish algorithm as the preferred option. This symmetric encryption algorithm makes use of a block cipher, just like Blowfish does.
DES
IBM and the National Security Agency collaborated in the early 1970s to develop the Data Encryption Standard, or DES. It is fine, but a poorly funded organization called the Electronic Frontier Foundation can crack a single key in just three days. The inclusion of this algorithm is intended to be comprehensive.
IDEA
Xuejia Lai and James Massey are responsible for the development of the IDEA – International Data Encryption Algorithm. It can withstand both linear and differential analysis, is quite quick, and has a reputation for having a high level of security. Ascom-Systec Ltd. requires that you pay a royalty in order to use this for any purpose other than your own personal use.
The Future of Encryption
Encryption is used in many of the tech products and tools we buy every day, and it will continue to be a key part of keeping our computer games, VOIP phone calls, and video chats safe. If it can be sent or stored, it is likely encrypted or has access to encrypted data.
As technology changes, new kinds of encryption will be made and used. Hackers are getting better at what they do, which keeps the people who make these secure tools busy coming up with ways to stay ahead of the bad guys.
You can be sure that most reputable software and hardware tools are safe to use as long as you follow the manufacturer’s instructions and keep your equipment updated and in good shape. Even though bad things will happen, we can still rely on the most popular encryption types of today.
FAQs
What is the main purpose of encrypting something?
Encryption is used to protect privacy by turning a message into a code, which hides what it says. Integrity and authenticity are what digital signatures are all about. They show who sent a message and that it hasn’t been changed.
What is an example of encryption?
Encryption is an important way for people and businesses to keep hackers from getting to sensitive information. Websites that send credit card and bank account numbers, for example, encrypt this information to stop identity theft and fraud.
What kind of encryption does Wi-Fi network use?
There are three types of wifi encryption protocols: Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Wi-Fi Protected Access Version 2 (WPAv2) (WPA2). One thing that all of these encryptions do is protect the data on your network. The main difference between them is how well they do this.
What is the latest technology in data encryption?
Quantum cryptography is a way to encrypt and send information securely that is based on the laws of quantum physics. Most encryption systems use secret keys, which are usually strings of numbers that are made up at random and used to encrypt and decrypt data.
What is the latest standard for encryption?
AES. The United States government and other organisations use the Advanced Encryption Standard (AES), which is a trusted standard algorithm. Even though 128-bit AES is very effective, it also uses 192-bit and 256-bit keys for very demanding encryption tasks.
How do I know my encryption code?
On the main page of the interface, click the “Wireless Settings” link and scroll down to the “Security Encryption (WEP) Key” section. The Wireless Encryption Key is listed in the field labeled “Key 1.” The WEP key will be a string of both letters and numbers.
Can encrypted devices can be hacked?
Yes, encrypted information can be broken into.
Are all cell phones encrypted?
Both Android and iPhone devices now come with full encryption built in.
Wrapping up
In a digital world, it’s important to use encryption to keep private information, messages, and financial transactions private and safe. It protects the privacy of digital information that is stored on computers or sent over the internet. There are many ways to encrypt data, such as the Advanced Encryption Standard (AES), which is the gold standard for data encryption and is used all over the world, and the U.S. government standard.
ad


Comments are closed.